2FA VPN mobile-accessible SFTP server setup
If the above title even remotely excites you, congratulations and condolences! See the guide below for project components, tips, and configuration steps.
The Admiralty deployed an SFTP server in it’s home-based Command Center and configured it to be accessible through a 2FA app-based OTP VPN. After authenticating through the 2FA-VPN, users can now access the SFTP server from mobile devices and upload/download files.
Products used:
FotiGate 60E Firewall. I got this in exchange for listening to a sales pitch from FortiGate. $358 on Amazon. The Admiralty personally extends it’s gratitude to the Fortinet Corporation, and welcomes future overtures of lucrative corporate blog sponsorship.
FortiClient VPN app for Android (free edition)
FortiToken Mobile for Android (license for 2x tokens for 1 year included with firewall)
Bitvise SSH server for Windows (free version)
Cx File Explorer for Android (free)
Quad 9 External DNS Server (free)
Journey to the Attainment of Technical Glory
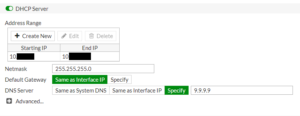 I configured the Fortinet firewall device and activated it as the gateway and DHCP server for my network. While researching which DNS server I wanted to deploy in the DHCP scope, I learned about the Quad-9 DNS Server (9.9.9.9), which automatically filters millions of malicious URLs and has a strong privacy policy. I deployed it as part of the DHCP scope. I registered and updated the firewall, which took multiple incremental upgrades, but went very smoothly.
I configured the Fortinet firewall device and activated it as the gateway and DHCP server for my network. While researching which DNS server I wanted to deploy in the DHCP scope, I learned about the Quad-9 DNS Server (9.9.9.9), which automatically filters millions of malicious URLs and has a strong privacy policy. I deployed it as part of the DHCP scope. I registered and updated the firewall, which took multiple incremental upgrades, but went very smoothly.
Roadblock: My PC’s networking wasn’t working right and it took a reboot of the PC to get it communicating. The other devices connected with much less issue. I have 2 NICS installed and a couple of virtual Hyper-V switches on my PC, so a configuration issue may have something to do with it. More on Virtualization and Hyper-V Networking in a future Admiralty communique!
[/show_more]
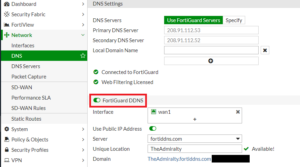 I setup Dynamic DNS (DDNS) that is built into the Fortigate (no additional cost). I have residential Cable on a dynamic IP that is currently costing me $45/month. To get a connection with a static IP, I’d have to pay $110 per month. So, I use the alternative of employing DDNS. I have a “(admiralyhostname).fortiddns.com” address that points to my dynamic IP. The domain name remains static and points to my IP. This lets me direct VPN connections to the hostname without having to modify them when my dynamic IP cycles. The built-in DDNS feature was amazingly easy to use and I much prefer it to having to sign up and use a 3rd-party DDNS service.
I setup Dynamic DNS (DDNS) that is built into the Fortigate (no additional cost). I have residential Cable on a dynamic IP that is currently costing me $45/month. To get a connection with a static IP, I’d have to pay $110 per month. So, I use the alternative of employing DDNS. I have a “(admiralyhostname).fortiddns.com” address that points to my dynamic IP. The domain name remains static and points to my IP. This lets me direct VPN connections to the hostname without having to modify them when my dynamic IP cycles. The built-in DDNS feature was amazingly easy to use and I much prefer it to having to sign up and use a 3rd-party DDNS service.
Fortinet, sponsor me and reign supreme over your cowering rivals. Cisco shall tremble in the wake of our mighty and lucrative Alliance.- I configured the VPN so that mobile users could connect to the network. This involved configuring
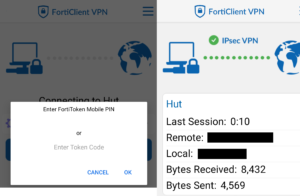 baseline VPN settings and the FortiToken 2FA system. Users use the Fortinet VPN client app along with the Fortitoken OTP code generator. The FortiToken app was easy to configure. I used the default SMTP server settings in order to send users registration emails, where they scan a barcode and add the OTP code. These went to their spam folders, as MX records were not configured, so the identity of the senders could not be verified. The SMS functionality did not work out of the box. This was a very small roadblock that can be corrected in future Admiralty Operations. I’m underwhelmed by the VPN client and may seek an alternative, but it functions. Fortinet, I forgive you of this transgression and will still wholeheartedly embrace your overtures of lucrative corporate sponsorship.
baseline VPN settings and the FortiToken 2FA system. Users use the Fortinet VPN client app along with the Fortitoken OTP code generator. The FortiToken app was easy to configure. I used the default SMTP server settings in order to send users registration emails, where they scan a barcode and add the OTP code. These went to their spam folders, as MX records were not configured, so the identity of the senders could not be verified. The SMS functionality did not work out of the box. This was a very small roadblock that can be corrected in future Admiralty Operations. I’m underwhelmed by the VPN client and may seek an alternative, but it functions. Fortinet, I forgive you of this transgression and will still wholeheartedly embrace your overtures of lucrative corporate sponsorship. - I tested connectivity between the VPN and LAN. This required a modification of the ever-pesky
 Windows firewall, whose entry for ICMP echo requests was “hidden”. Microsoft, thank you for providing me an opportunity to become more familiar with your intimate eccentricities. You continue to amaze me even after all these years. I tested some further functions on the FortiGate DNS server and decided to shelve this for another Journey of Glory, brought to you by the Fortinet Corporation (sponsorship pending).
Windows firewall, whose entry for ICMP echo requests was “hidden”. Microsoft, thank you for providing me an opportunity to become more familiar with your intimate eccentricities. You continue to amaze me even after all these years. I tested some further functions on the FortiGate DNS server and decided to shelve this for another Journey of Glory, brought to you by the Fortinet Corporation (sponsorship pending). 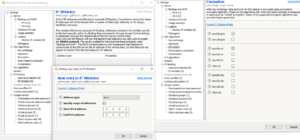 I setup the SFTP server software on my PC. After toying with Filezilla and lacking complete Fortinet-levels of satisfaction, I decided to give Bitvize a chance. The Admiralty was greatly pleased at the addition of this powerful new ally into The Fleet. The interface is swift to navigate, and configuration is intuitive. The granularity of the security settings, if you choose to rush in where n00bs fear to tread, surpassed the hopes of even The Admiralty’s most optimistic forecasters. You can select which elements of the cipher suites you want to allow or disallow. Whitelisting by IP, or CIDR block, is easily configurable. At Premium level, you can integrate with Active Directory. I setup and ultimately successfully tested an SFTP connection over the LAN from a laptop. Bitwise, The Admirality salutes you for offering a powerful freemium product that was instrumental to the success of this operation. Your contributions have been noted in the annals of our lore and will not be easily forgotten.
I setup the SFTP server software on my PC. After toying with Filezilla and lacking complete Fortinet-levels of satisfaction, I decided to give Bitvize a chance. The Admiralty was greatly pleased at the addition of this powerful new ally into The Fleet. The interface is swift to navigate, and configuration is intuitive. The granularity of the security settings, if you choose to rush in where n00bs fear to tread, surpassed the hopes of even The Admiralty’s most optimistic forecasters. You can select which elements of the cipher suites you want to allow or disallow. Whitelisting by IP, or CIDR block, is easily configurable. At Premium level, you can integrate with Active Directory. I setup and ultimately successfully tested an SFTP connection over the LAN from a laptop. Bitwise, The Admirality salutes you for offering a powerful freemium product that was instrumental to the success of this operation. Your contributions have been noted in the annals of our lore and will not be easily forgotten.- Next, I needed to get SFTP transfers working from an Android device on LAN as well as VPN.
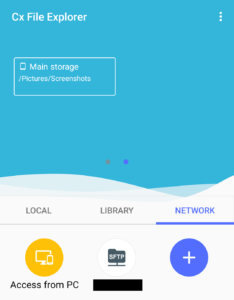 After a couple of misses, I decided to try a File Manager program with SFTP functionality rather than a more narrowly-tailored client. This was not the first choice of the Admiralty, as overly complicated programs that constantly scan file systems go against the axioms of Admiralty operations. Instead, CX File Explorer astounded me and was instrumental to the success of Operation SFTP. The program enables end-users to more easily locate the files for transfer and easily connect to a pre-configured FTP location. This worked smoothly on both LAN and VPN connections. Cx File Explorer, you have won yourself a powerful ally and protector in this quadrant.
After a couple of misses, I decided to try a File Manager program with SFTP functionality rather than a more narrowly-tailored client. This was not the first choice of the Admiralty, as overly complicated programs that constantly scan file systems go against the axioms of Admiralty operations. Instead, CX File Explorer astounded me and was instrumental to the success of Operation SFTP. The program enables end-users to more easily locate the files for transfer and easily connect to a pre-configured FTP location. This worked smoothly on both LAN and VPN connections. Cx File Explorer, you have won yourself a powerful ally and protector in this quadrant. - I wanted to add file-level encryption to files that were sent to the PC. I employed AxCrypt for this task. Program functionality is straightforward: you login to the program, and from the right-click context menu,
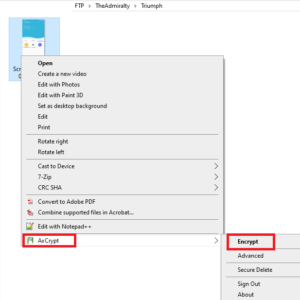 can encrypt or decrypt files. The premium version is (supposed to) scan selected folders and encrypt their contents. The software did not pass The Admiralty’s rigorous battery of testing regimes, and the Axcrypt Corporation has not yet won the sworn protection of The Admiralty. Automatic file locks of folders appear to work on restart of the PC. I submitted a ticket to their support and researched other solutions. The AxCrypt Corporation may still earn the right of protected vassalage to the might of The Admiralty pending resolution of this issue. The Admiralty sought another solution for file-level encryption. I discovered that I did not have a Trusted Platform Module, which is a motherboard component used to generate and store encryption keys. It is heavily involved in system-level encryption. One was purchased for $25. The Admiralty expended additional energy credits ($10 in so-called “currency”) to purchase one from the manufacturer of the motherboard, Gigabyte. Be cautioned, Gigabyte: should you fail us here, you may rue yourself the protection of a powerful ally.
can encrypt or decrypt files. The premium version is (supposed to) scan selected folders and encrypt their contents. The software did not pass The Admiralty’s rigorous battery of testing regimes, and the Axcrypt Corporation has not yet won the sworn protection of The Admiralty. Automatic file locks of folders appear to work on restart of the PC. I submitted a ticket to their support and researched other solutions. The AxCrypt Corporation may still earn the right of protected vassalage to the might of The Admiralty pending resolution of this issue. The Admiralty sought another solution for file-level encryption. I discovered that I did not have a Trusted Platform Module, which is a motherboard component used to generate and store encryption keys. It is heavily involved in system-level encryption. One was purchased for $25. The Admiralty expended additional energy credits ($10 in so-called “currency”) to purchase one from the manufacturer of the motherboard, Gigabyte. Be cautioned, Gigabyte: should you fail us here, you may rue yourself the protection of a powerful ally.